What Is Meant Bywhich of the Following Best Describes Pharming
Symantec developed the technique in conjunction with Indiana University as a proof-of-concept exploit that could result in identity theft or other unwanted results such as denial of. Software that communicates information from a users system without notifying the user.

Pharming Attack An Overview Sciencedirect Topics
A definition of spear-phishing.
. Spear-phishing is a targeted attempt to steal sensitive information such as account credentials or financial information from a specific victim often for malicious reasons. 1 Question 2. Pharming occurs when.
An action that exceeds the storage-space allocation of an application. Multiple Choice Questions and Answers on Animal Breeding and Transgenic Animal Question 1. Pharming may cause users to find themselves on an illegitimate website without realizing they have been redirected to an impostor site which may look exactly like the real site.
Put simply a SQL injection is when criminal hackers enter malicious commands into web forms like the search field login field or URL of an unsecure website to gain unauthorized access to sensitive and valuable data. Pharming is a malicious website that resembles a legitimate website used to gather usernames and passwords. A URL Uniform Resource Locator as the name suggests provides a way to locate a resource on the web the hypertext system that operates over the internet.
This is achieved by acquiring personal details on the victim such as their friends hometown employer locations they frequent and what they have recently bought. Act of attempting to acquire sensitive information by posing as a trustworthy entity. Phishing is a cybercrime in which a target or targets are contacted by email telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information banking and credit card details and passwords.
An eavesdropping attack is the theft of information from a smartphone or other device while the user is sending or receiving data over a network. A program disguised as a useful application. How to use phishing in a sentence.
Malware is a blanket term for viruses worms trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. James takes the falsified deed to a lender and borrows money against the property. 3T3 BHK HeLa BTK Answer.
Not to be confused with Fishing or Pishing. Question is Animal pharming can be defined as Options are A growing animals for farming B programming animals to produce novel products C generating transgenic animals for farming D none of the above E Leave your comments or Download question paper. The first part of a URL identifies what protocol to use.
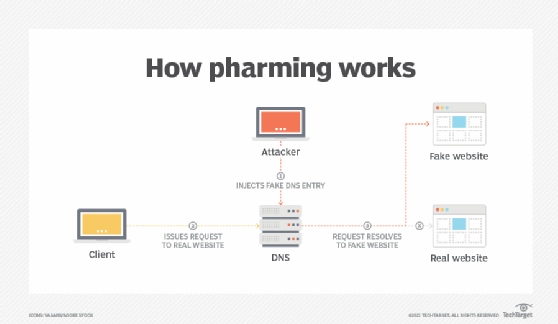
Pharming is a type of cyberattack involving the redirection of web traffic from a legitimate site to a fake site for the purpose of stealing usernames passwords financial data and other personal information. The process by which the major land masses have shifted their positions changed shapes and separated from each other is known as Continental drift. Make sure that website urls are correct and legit.
Cloning is a method by which numbers of genetically identical organisms are derived from a single organism by. Jump to navigation Jump to search. Which of these established cell lines originate from a mouse embryo.
3 Question 3. Pharming involves re-directing you to a malicious website which attempts to steal personal data. Imagine going to your favorite online clothing site.
As head of sales Jim is the data owner for the sales department. The information is then used to access important accounts and can result in identity theft and. Which of the following best describes Jamess.
Which of the following best describes the relationship between CobiT and ITIL. The URL contains the name of the protocol to be used to access the resource and a resource name. Eavesdropping attacks can be prevented by using a.
To alert management to the risk behind using a lower version of Kerberos he needs to explain what an attacker can do to leverage the vulnerabilities in it. Drive-by pharming is a vulnerability exploit in which the attacker takes advantage of an inadequately protected broadband router to gain access to user data. A program designed to attach itself to other code and replicate.
Please answer the following multiple 25 questions correctly and provide the answers below on Asset Security. CobiT provides a corporate governance roadmap whereas ITIL is a customizable framework for IT. The meaning of PHISHING is the practice of tricking Internet users as through the use of deceptive email messages or websites into revealing personal or confidential information which can then be used illicitly.
A system by which the bank verifies checks presented for payment against the list provided by the company of approved checks written on the account. Spoofing describes a criminal who impersonates another individual or organization with the intent to gather personal or business information. Which of the following best describes a virus.
Pharming refers to redirecting website traffic through hacking whereby the hacker implements tools that redirect a search to a fake website. A vulnerability assessment engineer performed vulnerability scanning on active directory servers and discovered that the active directory server is using a lower version of Kerberos. Pharming differs from phishing in that in a pharming scheme.
The nucleous of mature unfertilized ovum may be removed by irradiation surgery both 1 and 2 neutralization and homogenization Answer. URL Uniform Resource Locator. Although not well understood the Cambrian Explosion most likely occurred due to changes in sea level and continental drift.
CobiT is a model for IT governance whereas ITIL is a model for corporate governance. An example of a phishing email disguised as an official email from a fictional bank.

Pharming Attack An Overview Sciencedirect Topics

Solved 10 Points Question 1 While Browsing Online You Were Chegg Com
No comments for "What Is Meant Bywhich of the Following Best Describes Pharming"
Post a Comment